Cybersecurity Newsletter Vol. 2
VOLUME 2
Your Data, Their Profit

WhatsApp users, here is a fast-growing scam where crooks steal information, money, spread fake links, or send dangerous malware.
Bear with us — the fraud is confusing, which is why it’s so dangerous. Here’s how it works.
1: A hacker gets access to someone’s WhatsApp account.
They do this by getting that person to accidentally give up their 6-digit WhatsApp verification code (just like what they’re about to try with you). Now the hacker has full control of your friend’s account — they can see messages, contacts, and send messages as if they were that person.
2: Next, the hacker sends YOU a message pretending to be your friend.
Since they’re using your friend’s real account, the message looks legit. It says something like: “Hey! I accidentally sent a code to your phone instead of mine”. Can you send it to me?
3: But wait! That 6-digit code was actually sent to YOU by WhatsApp.
At the same time, WhatsApp sends you a message with a 6-digit login code — because the hacker tried to log into WhatsApp using your phone number.
4: If you share that code, the hacker can now log into your account!
That code is like a key to your WhatsApp. If you hand it over, the hacker takes over your account. You get logged out — and now the hacker is messaging your contacts, pretending to be you.
The hacker then uses your account to target your friends.
The lesson: don’t ever respond to an unexpected authentication message.

Android phone and tablet owners: Watch for a new security feature in the next few weeks. If you leave your device locked for three consecutive days, it will automatically restart. This is a smart move.
A restart is often needed to complete a system update or security patch. If someone hasn’t restarted their phone in days, this auto-restart helps keep the device updated and protected from threats.
Another benefit to automatic restarts: Some malware can survive in memory as long as the phone stays on. Restarting clears temporary data and can stop some types of malicious activity from continuing undetected.
Phone users: You should turn your phone off and back on every so often, too.
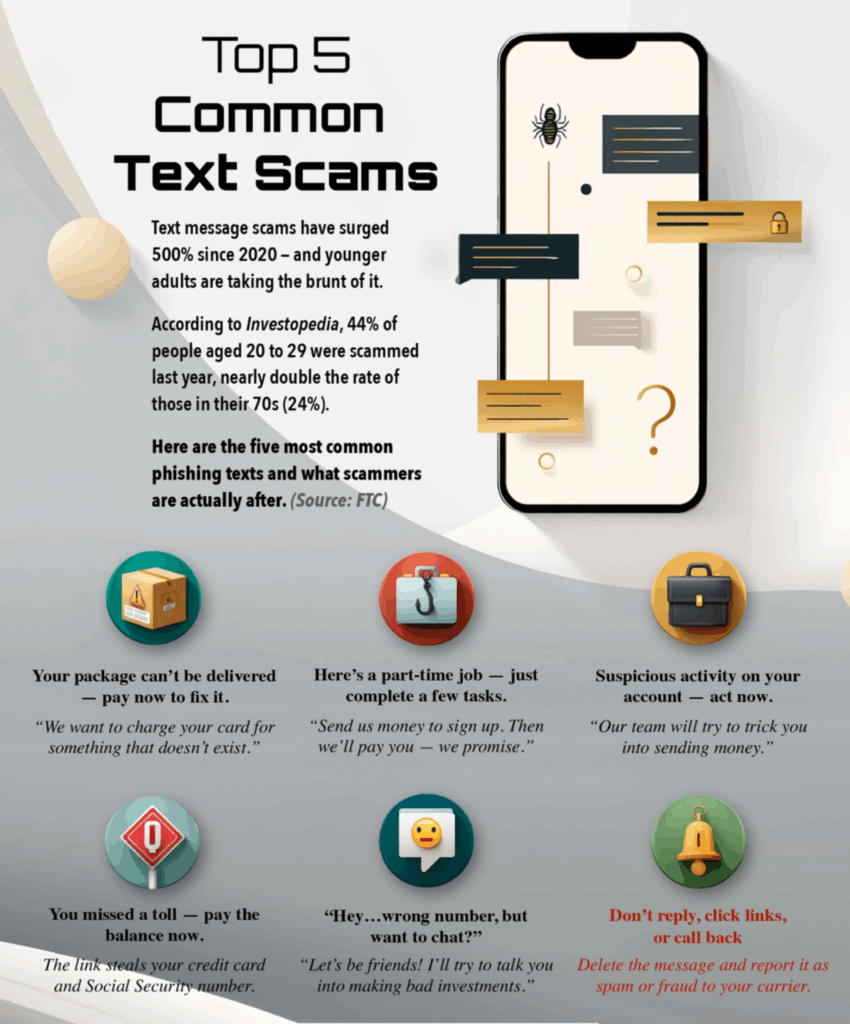
Common Cybersecurity Questions
“I got an email from Apple saying someone had added me as a trusted contact, but I don’t know what that is or who they are. What should I do?”
You can find out by following this path on your iPhone: Tap Settings [the icon that looks like a gear] > [Your name, where it appears at the top] > Privacy & Security (or Sign In & Security) > Account Recovery. If you don’t recognize a name there, you can delete it.
It’s not much of a danger because they won’t have access to your iPhone. If they get locked out of their Apple account, they can have a code sent to you, and use that code to get back in.
“Last time, you posted an answer about how anti-virus software can help keep my computer safe. Is that all I need?”
On your home computer, anti-virus software is an extra layer of security designed to catch threats your computer’s operating system might not. But more cybercrimes happen because we fall for scams based on the message in an email, text, or voicemail. Software won’t always help.
If you get an urgent communication, resist the urge to believe you’re in trouble. That warning or credit card charge is more likely a fake, even if it looks genuine. To check, visit the company’s website yourself — don’t click on a link to verify it.
“We’re about to head out on vacation. Is it safe to use public Wi-Fi at airports or coffee shops?”
Public Wi-Fi can be risky. Hackers can intercept data you send and receive on unsecured networks. Avoid logging into financial or sensitive accounts while you’re on public Wi-Fi, and use a VPN (Virtual Private Network) app if you need to connect. But whenever possible, use your phone’s hotspot as a way to connect your computer to the web instead.
Cybersecurity News from Citizens Business Bank
Always Keeping You Safer Online